In today’s How to Automate, we will learn how to automate Have I Been Pwned to check for hacked email addresses in your organization regularly and, if needed, take action.
Data breaches and email hacks are common. In fact, it is the most common way for attackers to gain access to your networks and systems. As said thousands of times, with cybercriminals actively seeking personal information, ensuring that your email address and online accounts remain secure organization-wide is critical.
However, there are no silver bullets. Otherwise, attacks would be much more exceptional. Still, as of today, the main entry point is through legitimate accesses, such as business email compromises (BEC), that have been compromised by attackers, notably through phishing attacks.
How to defend against it? Preventive measures would be enforcing strong passwords in the organization and enforcing 2FA for critical, logical accesses. Still, as long as you are not able to shoulder peek every employee to check if they have registered an effectively strong password and not the first 20 characters of the alphabet, you must adopt proactive measures.
One way to do this is by checking across your organization for hacked email addresses has been compromised using the popular online service Have I Been Pwned. A traditional way to do it is to run regular checks on Have I Been Pwned or perform scans following new breach releases. Although critical, this workflow can be repetitive and time intensive as your organization grows and more employee accounts are to be checked.
The good news is, thanks to Mindflow, you can easily automate this process to save time and ensure you’re always up to date with potential security risks. In this blog post, we’ll explain how to automate the monitoring for hacked email addresses by using Have I Been Pwned and then take action on the findings.
We will orchestrate 3 tools: Have I Been Pwned, Google through Google Admin Directory SDK API, and Slack.
Have I Been Pwned automation for hacked email addresses overall goal
The main goal is to create a scheduled Flow that would run twice a week, at the beginning of the week and at the end.
Following the results, we will predetermine remediation actions through Google Admin Directory SDK API, such as Sign-in out the users from devices and web sessions, resetting sign-in cookies, and also requesting a password change at the next login. To notify your IT or Security team, we will generate a report to be posted on Slack.
Bear in mind that you can easily replace Google with Microsoft Office 365 adequate API and Slack with Google Chat, Teams, Emails, or even Jira, Opsgenie, and most of your communication tools.
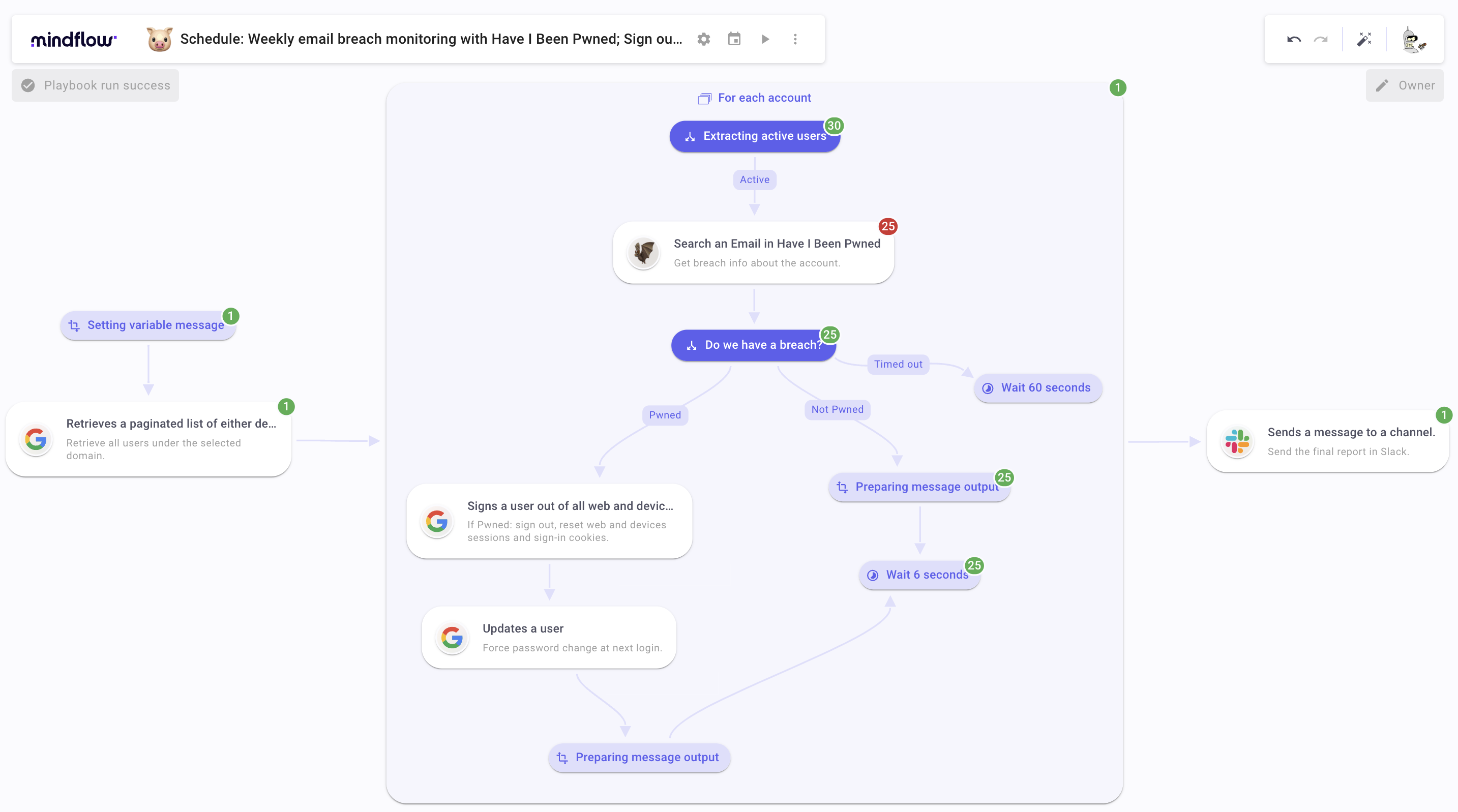
Here is a quick peek at the final Flow before we dive in.
We will divide the walkthrough into 4 sections, covering the building’s milestones.
To make it functional, you will need:
- Slack API credentials:
- Follow this link (and add your channel id in the URL) https://api.slack.com/apps/YOUR_CHANNEL_ID/oauth? and,
- If not done already, add the following permissions chat:write, chat:write.customize.
- Add the created bot on the desired channel.
- Google Admin Directory SDK API: add the following scope: https://www.googleapis.com/auth/admin.directory.user.
- Have I Been Pwned: API key registered here.
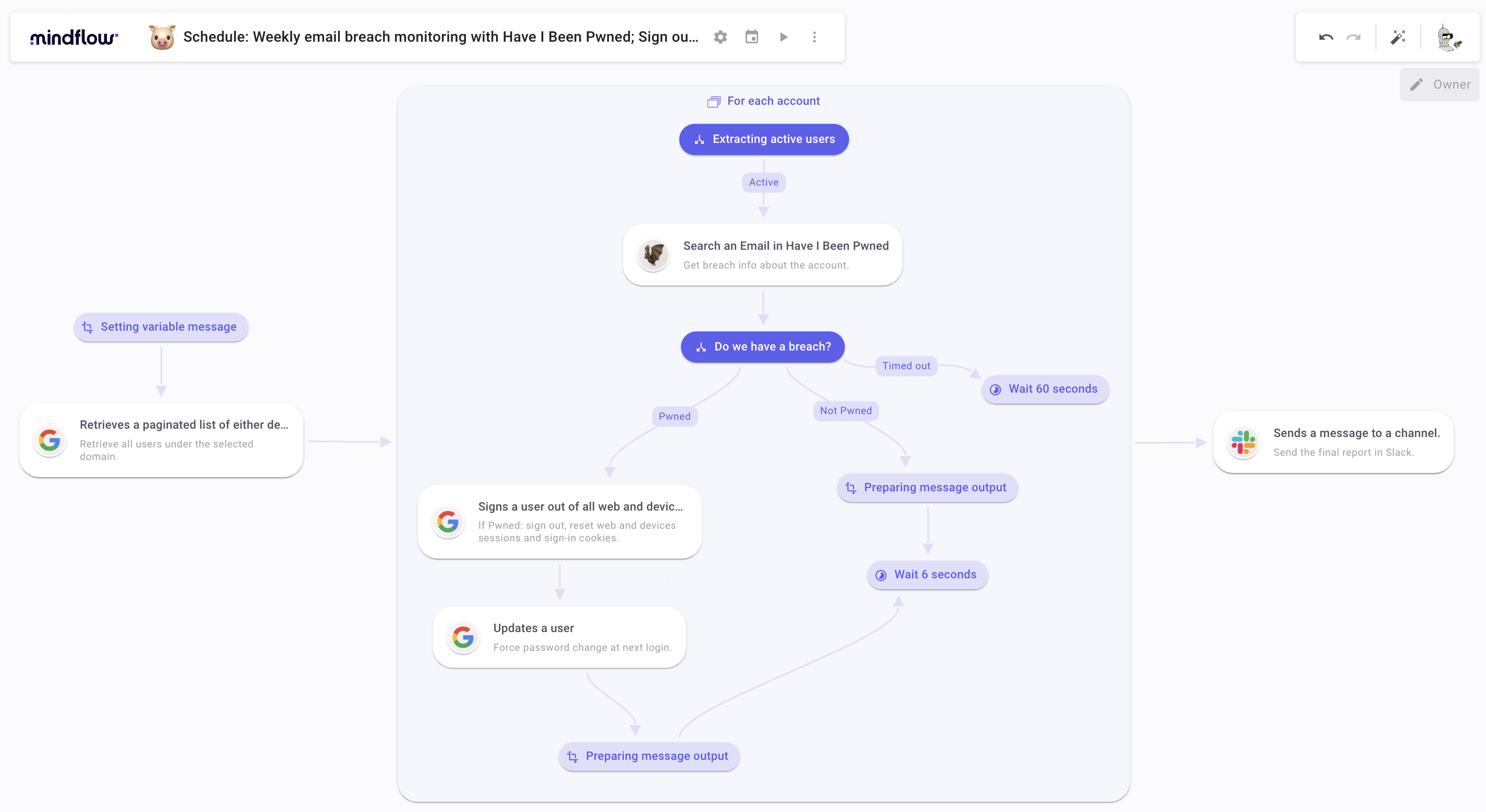
First steps to automate monitoring for hacked email addresses
Create the Flow and configure the schedule to automate the triggering on specific days
First of all, create the Flow, assign a name that may be cooler than the one we will give for the purpose of this article “Schedule: Weekly email breach monitoring with Have I Been Pwned; Sign out, Reset sign-in cookies and password at next login if needed” haha. Of course, choose your emoji! I chose a cute piggy face.
After having created the Flow, you have to set up the Scheduler. To do so, click on the calendar icon to open the Scheduler pop-over and:
- Set the trigger "At regular intervals".
- Select Weekly.
- Every Monday and Friday, at 9:02 a.m.
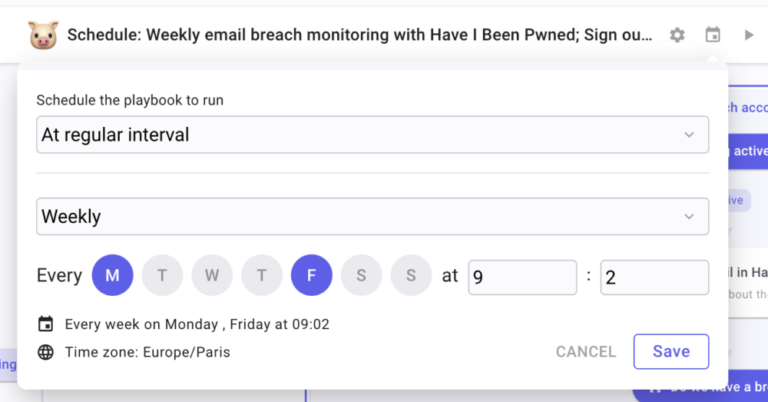
Set your variable
To be able to generate a nice report comprising all our iteration output, we have to set an empty variable that we will update for each iteration inside the For each loop. To do so, create a Transform Data. Name it Setting variable message. Inside, click on “Add an item” and name this item message. Leave it empty.
Retrieving all accounts before checking for hacked email addresses
Ensure you have your Google Admin Directory SDK API credentials registered in the Vault, either OAuth2 or Google Service Account; Mindflow handles both (Reminder to myself to write the overall guide for Google authentication! Stay tuned!).
- Get Google Admin Directory SDK API directory.users.lists call.
- Hard-type your domain.
For each account
Create a For each loop. Name it For each account. Set source by “/” and get in “Retrieves a paginated list…” the table users to iterate on.
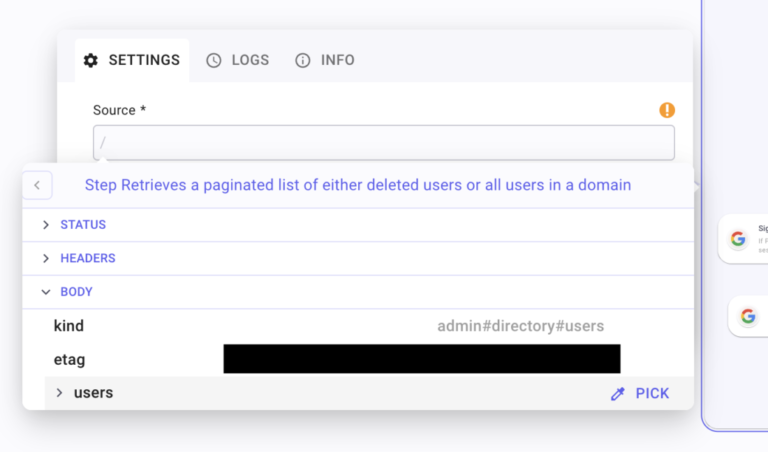
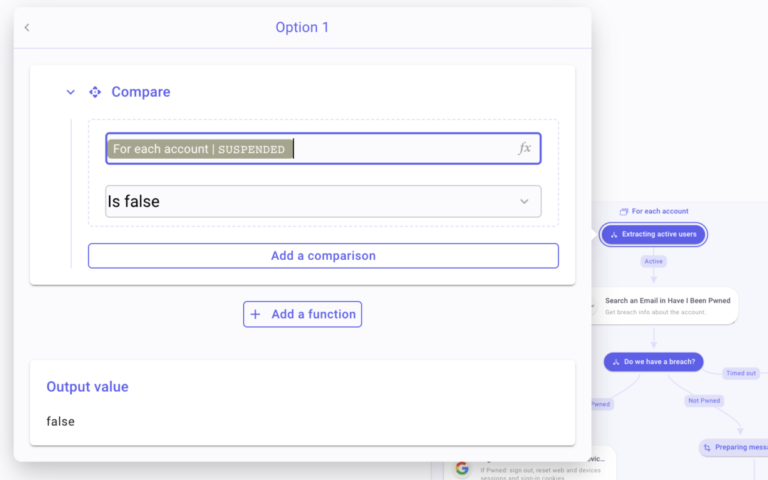
Create a condition Extracting active users to extract only active users. Inside this condition, create one branch, named Active: Create a compare function, “/” to Pick the field suspended. Set the operator to Is false.
Create an HIBP step by querying the get/api/v3/breachedaccount/{{email}}. Configure it as such:
- Important, if the account is not breached, HIBP will return a 404 Not Found. To avoid the Flow stopping upon failure. Change the “On failure” field to
Continue execution. - Under the URL field, https://haveibeenpwned.com/api/v3/breachedaccount/[TYPE “/” to Pick the field
PrimaryEmailin the Iteration Data in For each account under FLOW].
After the HIBP step, create a condition, name it Do we have a breach? and create 1 wait, 1 Transform Data, and 1 Google Admin Directory SDK API step by querying the directory.users.signOut call.
Configure the branches as such:
- To the Wait: Name the branch Timed out. Create a compare function and Pick under the HIBP step the field
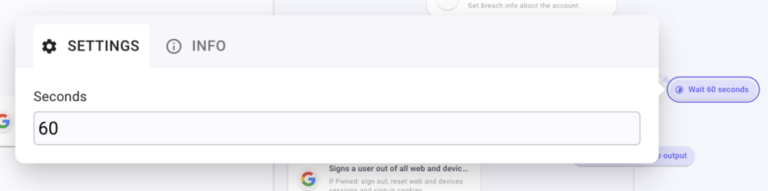
Codeunder STATUS. Select the operatorContainsand type “429”. Configure the Wait at 60 seconds and name it Wait 60 seconds. This branch is created to meet the Request per Minutes (RPM) limitation from Have I Been Pwned. According to the plan you subscribed to, you have a limited set of RPM. So, if the API request returns an error 429, we will just wait 60 seconds before iterating again.
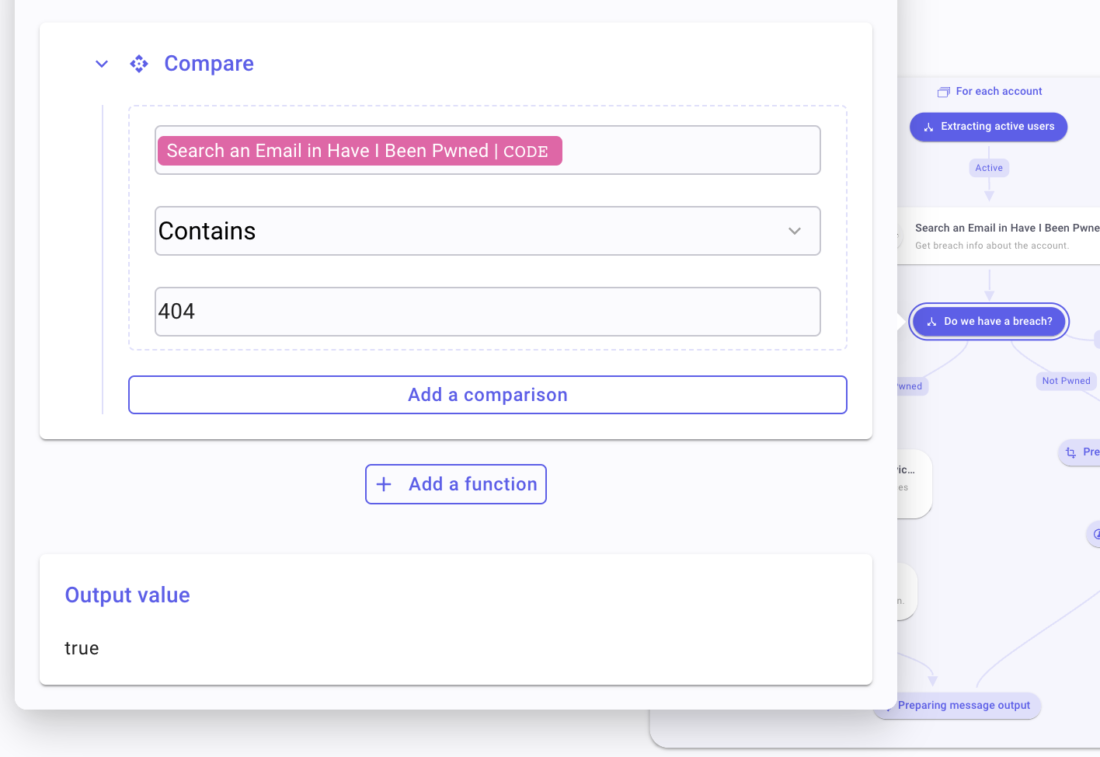
- To the Transform Data: Name the branch Not Pwned. Create a compare function and Pick under the HIBP step the field
Codeunder STATUS. Select the operatorContainsand type “404”. Rename the step Preparing message output. - To the Google step: Name the branch Pwned. Create a compare function and Pick under the HIBP step the field
Codeunder STATUS. Select the operatorContainsand type “200”.
On to the other steps.
Your first Wait step, Wait 60 seconds, is already configured. Hop on Preparing message output. Inside, create an item called message. After Preparing message output, create a new Wait step and set it to 6 seconds. Name it Wait 6 seconds. To limit the possibility of being timed out as we explained above, we create a Wait 6 seconds to ensure that we are not going to be timed out due to our current plan (yes, we have the less expensive one bcz we no rich yet! :-D).
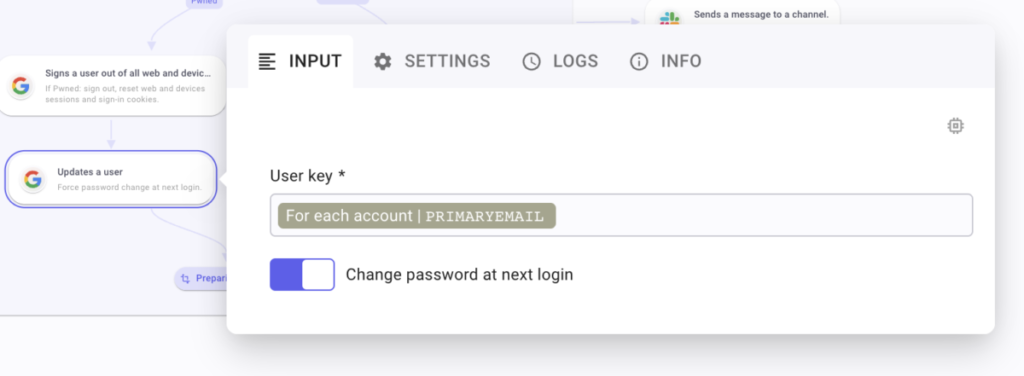
To configure the Google Admin Directory SDK API directory.users.signOut call, open the step’s settings panel, and, in the Input tab, under User key, Pick PrimaryEmail under For each account iteration data.
After this first Google step, create a new Google step by querying the path directory.users.update from the Google Admin Directory SDK API. Configure it by calling PrimaryEmail field under the For each account Iteration data. Ensure you enable the boolean “Change password at next login.” to True.
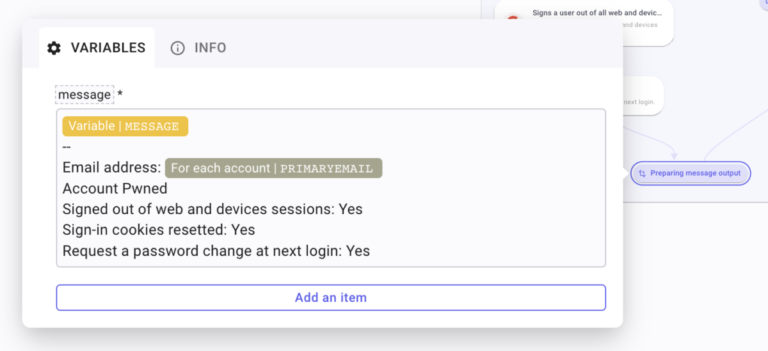
Create a Transform Data after this last step, named Preparing message output (yes, the same name as the first one, don’t worry, it doesn’t have consequences). Add an item and call it message. Type “–” to format the message and then the following chunks:
- Email address: Pick PrimaryEmail address under For each account iteration data.
- Account Pwned
- Signed out of web and devices sessions: Yes (hard-typed because the action will have already been performed in the previous step)
- Sign-in cookies reset: Yes
- Request a password change at the next login: Yes
Additional: You can add the date at which these actions have been performed by typing “/”, and selecting the “Retrieves calling the directory.users.signOut step and Picking date.
Once this second Preparing message output is created, link it to the Wait 6 seconds. To ensure that we are not going to be timed out, as we explained above.
Sending final report on Slack
After your For each account, you will have to create a Slack API call by querying the chat_postMessage action. Configure it as such:
- Channel: [YOUR CHANNEL ID].
- Text: "Here is your bi-weekly email breach report generated using Have I Been Pwned: ["/" to Pick message]".
The flow is set! You can manually run it once to see all the pills pop up and witness the rare phenomenon of red pills stacking up! Now you have your automated check for hacked email addresses and remediation using Have I Been Pwned!